An Introduction to Quantum-Resistant Cryptography
Post-quantum cryptography is a field of study focused on developing and implementing cryptographic algorithms that are resistant to attacks by quantum computers. With the advancement of quantum computing technology, it has become increasingly likely that traditional cryptographic methods, which are based on mathematical problems that are difficult for classical computers to solve but easy for quantum computers to solve, will become vulnerable to attacks. As a result, there is a pressing need for new cryptographic algorithms that can withstand attacks from quantum computers and ensure the security of sensitive information. In this context, post-quantum cryptography aims to design and implement cryptographic methods that are resistant to quantum attacks and can provide the necessary security for a post-quantum era.
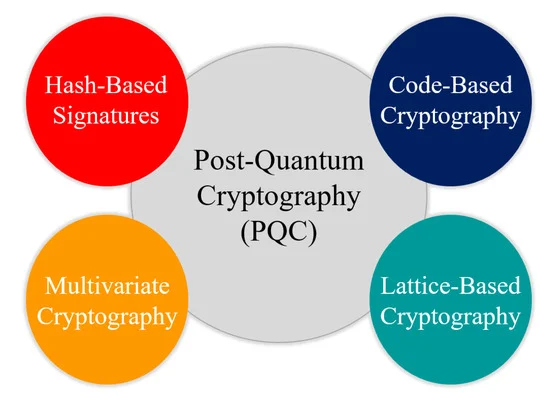
To protect against this possibility, researchers are developing new cryptographic techniques that are resistant to attack by quantum computers. Some examples of post-quantum cryptographic methods include lattice-based cryptography, multivariate cryptography, code-based cryptography, and hash-based cryptography. It is important to note that these methods are still in the development stage and have not yet been widely adopted.
Lattice-based cryptography
Lattice-based cryptography is a type of cryptography that is believed to be resistant to attacks by quantum computers. It is based on the mathematical properties of lattices, which are structures made up of points arranged in a grid-like pattern. Lattice-based cryptography is considered to be a promising option for the post-quantum era, as it is thought to be resistant to attacks by quantum algorithms that are able to break other forms of cryptography, such as RSA and ECC (Elliptic Curve Cryptography).
There are several different types of lattice-based cryptography, including NTRU (short for N-th degree Truncated Polynomial Ring Units), RLWE (short for Ring Learning with Errors), and LWE (short for Learning with Errors). These algorithms all work by generating a secret key based on the properties of a lattice, and then using this key to encrypt and decrypt messages.
One of the main advantages of lattice-based cryptography is that it is relatively easy to implement and requires relatively low computational resources. This makes it well-suited for use in resource-constrained environments, such as on mobile devices or in the Internet of Things (IoT).
Lattice-based cryptography is considered to be a promising option for the post-quantum era, as it is believed to be resistant to attacks by quantum computers and can be implemented with relatively low computational resources. However, it is still an emerging field and more research is needed to fully understand its potential and limitations.
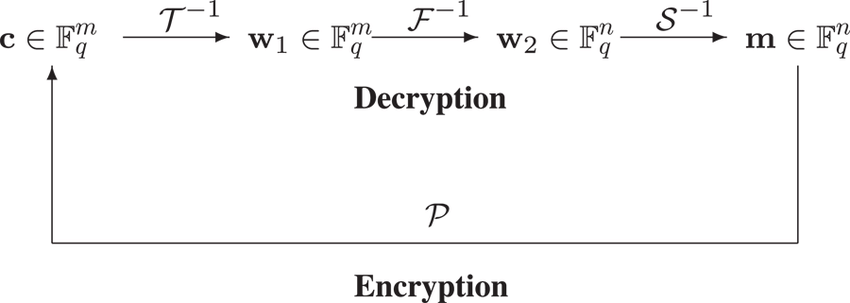
Multivariate cryptography
Multivariate cryptography refers to cryptographic techniques that use multiple variables as the basis for generating keys and encrypting/decrypting messages. These techniques are believed to be resistant to attacks by quantum computers, as they rely on mathematical problems that are believed to be hard to solve with quantum algorithms. Some examples of multivariate cryptography include McEliece and Niederreiter cryptosystems, which use the concept of algebraic error-correcting codes to generate keys and encode/decode messages. These systems are believed to be secure against attacks by quantum computers, as the mathematical problems they rely on (such as the decoding of error-correcting codes) are thought to be difficult for quantum algorithms to solve. However, it is important to note that the security of these and other multivariate cryptographic techniques is still being actively researched, and it is possible that they may be vulnerable to future attacks or breakthroughs in quantum computing.
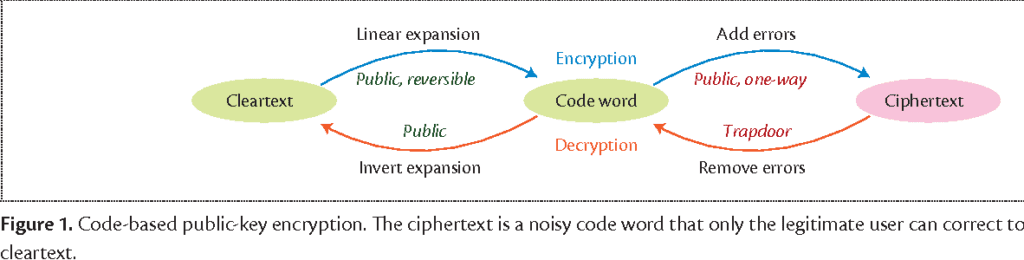
Code-based cryptography
There are several code-based cryptography algorithms that are believed to be resistant to attacks from quantum computers. These include McEliece, Niederreiter, and Goppa codes. These algorithms rely on the difficulty of decoding a message encoded using error-correcting codes, which makes them resistant to attacks even from powerful quantum computers. However, it is important to note that the security of code-based cryptography is not yet fully understood, and further research is needed to confirm their resistance to post-quantum attacks.
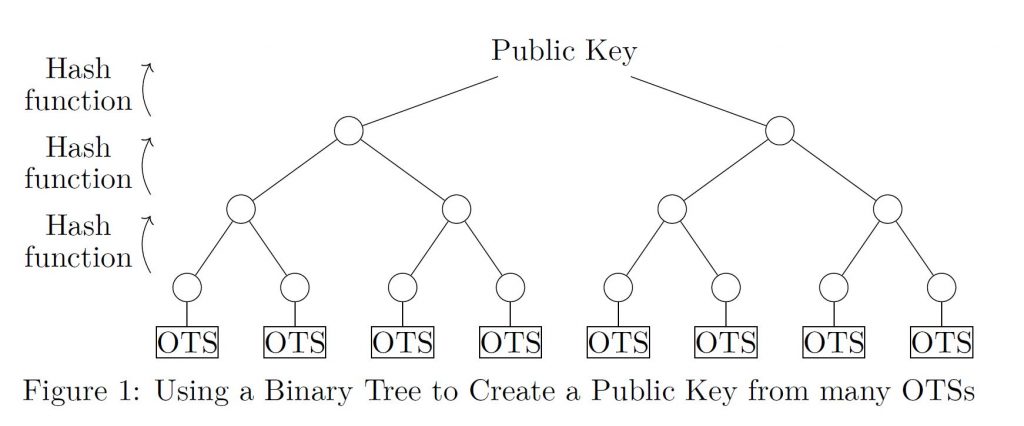
Hash-based cryptography
It is difficult to say definitively which specific hash-based cryptographic algorithms will resist the post-quantum era, as the field is still in the early stages of research and development. However, it is generally believed that hash-based cryptography, which relies on the difficulty of finding a collision (i.e., two different inputs that produce the same hash output) in a given hash function, has the potential to be quantum-resistant. This is because it is thought that finding collisions in hash functions using quantum computers may still be computationally infeasible, even in the post-quantum era. Some examples of hash-based cryptographic algorithms that have been proposed as potential candidates for quantum resistance include the Merkle-Damgård construction, the Sponge construction, and the HMAC construction. It is important to note, however, that the security of these and other hash-based cryptographic algorithms has not yet been rigorously tested against quantum attacks, and further research is needed to determine their true quantum resistance.
Conclusion
In conclusion, the potential for quantum computers to break current cryptographic methods has led to the need for post-quantum cryptography. Several options exist, including lattice-based, multivariate, code-based, and hash-based algorithms, which are resistant to attacks from quantum computers. It is important for organizations and individuals to start considering the transition to post-quantum cryptographic methods in order to secure their data and communications in the future.